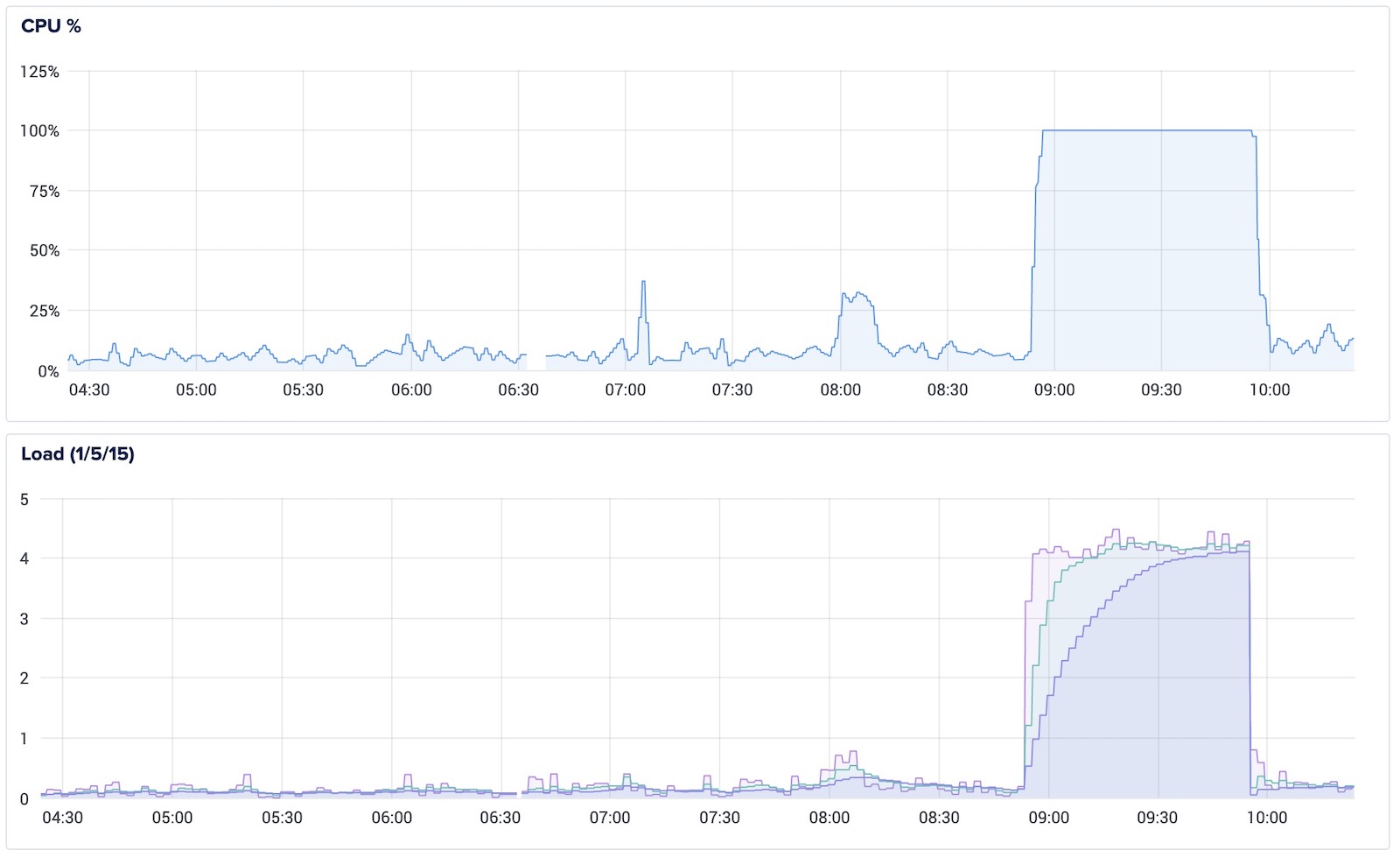
You must be here because your Self-Hosted server suddenly reports 100% CPU Utilization and making all server websites slow. There are lot of hackers who use brute-force attack on websites to gain access of it.
Let's start with list of defences:
1. Using different username apart from admin
Make Hackers Job More Difficult by choosing Site Specific Usernames
2. Use difficult Passwords with Alphanumerics along with spcial charactors like % # *
3. Disable xmlrpc.php which is exploted by hackers by DDOS Attacks
XML-RPC is feature of WordPress that enables data to be transferred with other systems like posting the articles from Mobile Apps. Most of the websites don't need this feature. It's better to block access to these file.
Edit file /etc/apache2/apache2.conf
<Files xmlrpc.php>
Order Deny,Allow
Deny from all
</Files>4. Enable Fail2ban for WordPress
Create a wordpress filter file wordpress.conf in /etc/fail2ban/filter.d/ with following content
[Definition]
failregex = ^<HOST> .* "POST .*wp-login.php
ignoreregex =Let's create a Fail2ban Configuration in /etc/fail2ban/jail.d/wordpress.conf
[wordpress]
enabled = true
port = http,https
filter = wordpress
action = iptables-multiport[name=wordpress, port="http,https", protocol=tcp]
logpath = /var/log/apache2/access*log
maxretry = 5
findtime = 3600
bantime = 1296000logpath- Apache Access log filemaxretry- Maximum number of failed password trials allowedfindtime- Time period within which maxretry limit is crossed. 3600 for 1 hour.bantime- Time in seconds for which IP will remain blocked. 1296000 for 15 days. -1 for Permanent block.
Once configuration is done you can check IP Blocking mechanism in log file /var/log/fail2ban.log
2021-09-13 10:15:27,078 fail2ban.filter [3412]: INFO [wordpress] Found 162.158.166.36
2021-09-13 10:15:27,412 fail2ban.filter [3412]: INFO [wordpress] Found 162.158.166.36
2021-09-13 10:15:27,774 fail2ban.filter [3412]: INFO [wordpress] Found 162.158.166.36
2021-09-13 10:15:28,106 fail2ban.filter [3412]: INFO [wordpress] Found 162.158.166.36
2021-09-13 10:15:28,447 fail2ban.filter [3412]: INFO [wordpress] Found 162.158.166.36
2021-09-13 10:15:28,467 fail2ban.actions [3412]: NOTICE [wordpress] Ban 162.158.166.36Restart service just to make sure that it's running well.
sudo service fail2ban restartReference: https://www.plesk.com/blog/various/using-fail2ban-to-secure-your-server/
How to unblock IP
fail2ban-client set wordpress unbanip 162.158.166.36How to add extra IP in Blacklist
fail2ban-client set wordpress banip 162.158.166.36Get banned IP's for wordpress filter
$ fail2ban-client status wordpress
Status for the jail: wordpress
|- Filter
| |- Currently failed: 142
| |- Total failed: 188
| `- File list: /var/log/apache2/access.log
`- Actions
|- Currently banned: 8
|- Total banned: 8
`- Banned IP list: 162.158.165.150 162.158.166.36 162.158.167.238 172.69.135.210 172.69.135.216 198.204.234.254 66.115.176.18 172.68.144.56How to top 10 IP's from which requests are made
Note: Make sure to ignore your own IP and IP of Server.
awk '{ print $1}' /var/log/apache2/access.log | sort | uniq -c | sort -nr | head -n 10This is for now. We wil be adding more such defence techniques soon...









Leave a Reply